Course Description
All BCIT students are required to submit a Computer Project/Dissertation at the end of their programme.The project will be specified, designed and implemented, with one of the Professors/ Lecturers as adviser/ supervisor.
Course Objectives
To give the student practical experience in developing and implementing non-trivial programming/ research projects based on the skills they learnt during their programme.
Course Learning Outcomes
By the end of the lecture the student will be able to
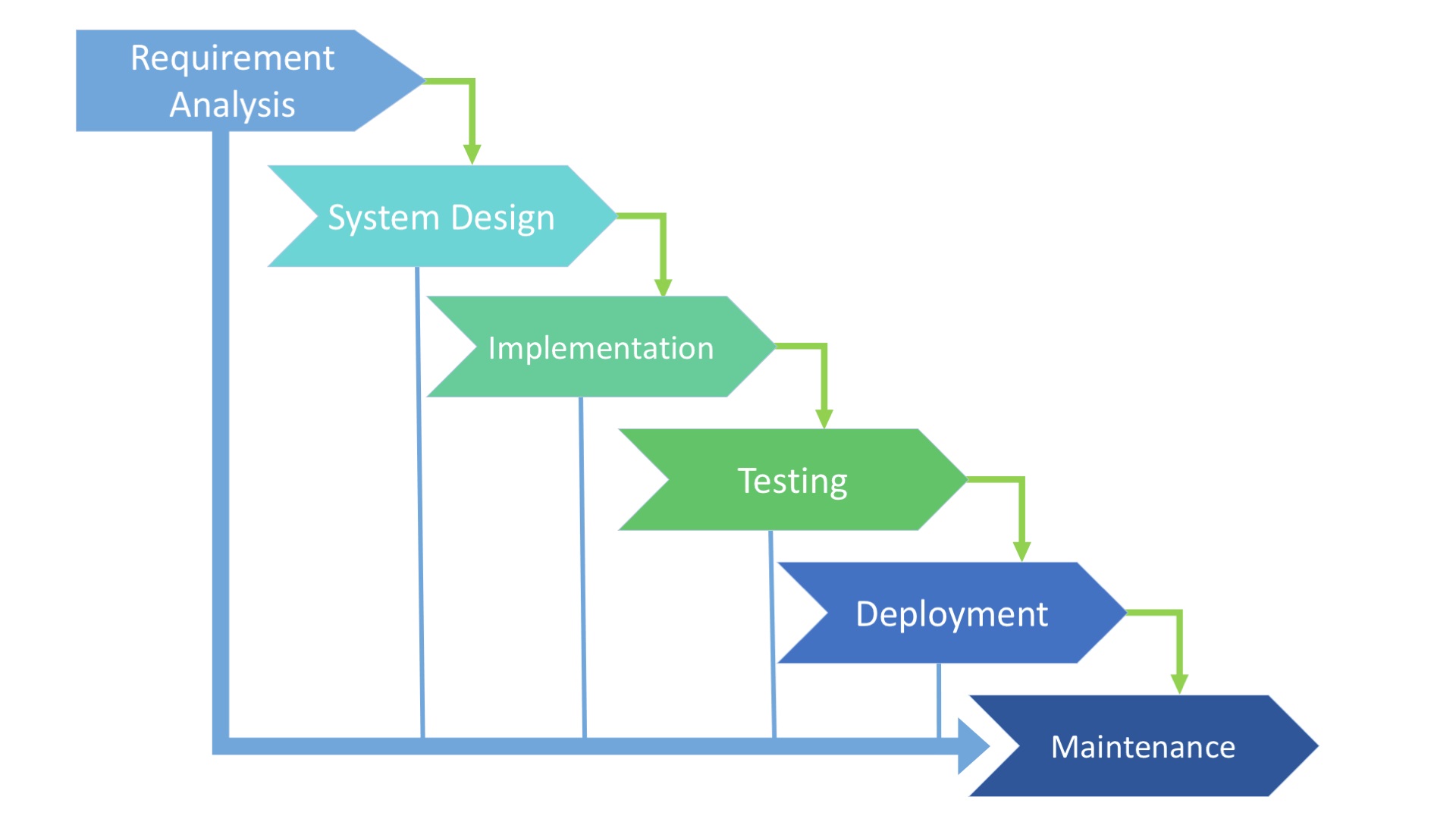
- Analyse a problem to identify and define the computing requirements appropriate to its solution.
- Design, implement, and evaluate a computer-based system, process, component, or program to meet desired needs.
- Present a complete IT project report at the end of the second semester of year III.
Detailed Course Content
1. Planning for an IT Project (5 hours)
i) Selecting a topic
Objective and the research question
ii) Supervision
2. Literature Review (10 hours)
i) Reading in the library, the Internet, note taking, observation
ii) Existing Information system
iii) Weaknesses of existing systems
1. Methodology (33 hours)
Problem identification
Fact finding methods:
i)Questionnaire
-Designing and administering a questionnaire
-Primary and secondary sources of data
-Data analysis using statistical packages
ii)Interview
iii)Observation
-Problem analysis
-Functional requirements
-Non functional requirements
-System designing
System design tools
User interface design, input and output design
Databases design
-Programing
-Testing and implementation
-Validation
IT project Report Writing (12 Hours
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, class discussions, case studies, class presentations, class demonstrations, independent studies
Mode of Assessment
i) Presentation = 30 %
ii) Final examination = 70%
iii) Total = 100%
Reading List:
Bell Judith (2005), Doing your Research Project. A Guide to First Time Researchers in Education, Health and social sciences. 4th Edition.
- Teacher: Emmanuel Eilu
Course Description
This course introduces the concept of security in operating system and software/web interfaces, and gives a brief overview of applications of cryptography. Main subjects are models and implementation of authentication, identity and access control mechanisms, theory of exploits and malicious software, techniques for mitigating these threats and how to develop a very good web interface. The course intends to give students an understanding of the principles of securing a computer system. These include insight in security policies, mechanisms and vulnerabilities in operating system and software/web sites. The course will also give insight into methods for development and test of security in software.
Course Objectives
1. To introduce to students the principles of securing a computer system.
2. To provide knowledge and understanding about the mechanisms and vulnerabilities in operating system and web sites.
3. To equip students with the practical skills of developing and testing security in software.
Course Learning Outcomes
On the completion of this course students will be able to:
1. Understand the principles of securing a computer system.
2. Describe mechanisms and vulnerabilities in operating system and web sites.
3. Develop an insight into methods for development and test of security in software.
Indicative Content
1. Introduction to securing an operating system (5 hours)
2. Security: (15 Hours)
i) General Definitions,
ii) Role of the Operating System,
iii) Security Policies,
iv) Confinement of Information,
v) Principle of Least Authority,
vi) Operating System Security,
vii) Requirements for Implementing a Secure Operating System,
viii) Supporting Hardware, Computer System Environment.
3. Security Services Provided by the Operating System; (15 Hours)
i) Resource Security,
ii) Service Security,
iii) Communication Security,
iv) Operating System Design Options,
v) Access Control Lists,
vi) Capabilities, Capability Implementations,
vii) Tagged, Segregated, Encrypted, Password,
viii) Theory of exploits and malicious software,
ix) Techniques for mitigating these threats and how to develop a very good web interface.
4. The Future of Operating Systems. (5 Hours)
5. The Characteristics of Successful web User Interfaces: Clear, Concise, Responsive, Consistent, Attractive and Forgiving are to be discussed. (20 Hours)
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lecturer, Tutorial, Lab sessions, Case studies
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
1. Securing the Operating System and the Interfaceby Thomas Shinder [Published on 17 July 2002 / Last Updated on 17 July 2002]
2. A Web Developer's Guide to Securing a Server (Web Security Topics) by Nigel Chapman and Jenny Chapman. Paperback – November 22, 2011

- Teacher: Emmanuel Eilu
Course Description
This is a specialized Course Unit in information systems and information technology (IS/IT) for undergraduate MIS majors. The Course Unit is targeted to senior MIS students who want more expertise in developing, managing and using Decision Support Systems. It examines the design, development and implementation of information technology based systems that support managerial and professional work, including Communications-Driven and Group Decision Support Systems (GDSS), Data-Driven DSS, Model-Driven DSS, Document-Driven DSS, and Knowledge-Driven DSS.
Course Objectives
- To introduce to students the structures, modelling, and the application of various decision support systems in today's corporate environment.
- To provide knowledge and understanding of decision support systems. Problems formulation. Linear programming and parametric programming, and their applications including transport and assignment problems. Inventory problems. Replacement, maintenance and reliability problems. Dynamic programming. The principles of optimality. Decision trees. Critical path planning
3. To provide knowledge and practical skills for computer support for organizational decision making, and various planning, analysis and control tasks.
- To enable students examine user interface design issues and evaluate the user interfaces and capabilities of Decision Support Systems.
Course Learning Outcomes
By the end of the lecture the student will be able to:
1. Identify structures, modelling, and the application of various decision support systems in today's corporate environment.
2. Identify the characteristics of decision support systems. Problems formulation. Linear programming and parametric programming, and their applications including transport and assignment problems. Inventory problems. Replacement, maintenance and reliability problems. Dynamic programming. The principles of optimality. Decision trees. Critical path planning
3. Examine examples and case studies documenting computer support for organizational decision making, and various planning, analysis and control tasks.
4. Examine user interface design issues and evaluate the user interfaces and capabilities of Decision Support Systems.
Indicative Content
1. Managerial decision making and information systems: (12 Hours)
i) Nature of managerial work and productivity;
ii) defining management information needs;
iii) requirement for decision support for decision making and other executive work;
iv) types and levels of support systems.
2. Decision Support Systems (DSS): (12 Hours)
i) DSS characteristics and capabilities;
ii) DSS taxonomies and frameworks;
iii) decision modeling using multi-criteria decision making;
iv) model management for decision support;
v) DSS development tools;
vi) DSS development approaches;
vii) DSS analysis and design methods;
viii) DSS documentation tools;
ix) case studies of DSS development.
3. Executive Support Systems (ESS). (6 Hours)
i) Executive information systems (EIS) and executive support;
ii) executives' information needs; ESS/EIS tools;
iii) use of ESS for office support applications;
iv) use of ESS in planning and control;
v) system development and EIS implementation.
4. Group Decision and Negotiation Support Systems (GDSS, NSS): (6 Hours)
i) Goal of GDSS and its levels;
ii) technology of GDSS, computer support for collaborative problem solving in meetings;
iii) electronic meeting systems to support group work;
iv) GDSS software; idea generation;
v) negotiation support systems;
vi) mediators and facilitators;
vii) construction of a GDSS and determinants of its success;
viii) support system for cooperative work.
5. Expert Systems (ES): (6 Hours)
i) Introduction to expert systems;
ii) introduction to logic, knowledge engineering and knowledge acquisition;
iii) knowledge representation and inference;
iv) knowledge encoding;
v) issues and methods in verification and validation of expert systems;
vi) expert systems applications in management and finance.
6. Intelligent Decision Support Systems: (6 Hours)
i) Knowledge-based decision support systems;
ii) intelligent DSS systems design with integration of expert system, hypermedia, and database technology;
iii) case-based decision aiding systems, active decision support system and symbiotic systems;
iv) neural networks, integration of expert systems and neural networks;
v) integrated intelligent systems.
7. Implementation of Support Systems: (6 Hours)
i) Implementation successes versus failures;
ii) technical versus human factors in implementation;
iii) cost justification methods : value analysis, usability analysis;
iv) implementation and sponsorship roles;
v) linking systems to organizational objectives;
vi) managing organizational resistance;
vii) managerial participation versus involvement;
viii) organizational and societal impacts of computer-based support systems.
8. Data mining and knowledge discovery systems: (6 Hours)
i) Tools based on statistical and other techniques that are used to extract information and possible creation of knowledge from large and very large databases.
ii) Quantitative models, like statistical or management science models, are often the core of decision support systems.
9. Decision making requires knowledge and expertise. (6 Hours)
Cognitive mapping and soft system approaches are used to build models of human knowledge and problem representation.
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Tutorials, Lab sessions, Case analysis
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List
- E. Turban and J. Aronson, Decision Support Systems and Intelligent Systems, 5th edition, Prentice Hall, 1998.

- Teacher: Emmanuel Eilu
Course Description
This course covers the technical concepts of data networks, network components, associated network technologies, and data communications protocols. It also comprises of the emerging technologies in data communications such as 3G, 4G, wireless networks among others. It targets network engineers, professionals from different IT fields, fresh graduates, business personnel, CIO.
Course Objectives
1. To examine the all the layers of the OSI reference model and the services that take place therein.
2. To identify the emerging technologies in data communication and how they are being integrated or applied.
3. To apply the layers into their respective organizations or places of work.
Course Learning Outcomes
By the end of the lecture the student will be able to:
- Operate with new emerging technologies in networking and data communication,
- Demonstrated the knowledge of detecting and rectifying the errors on different transmission media,
- Demonstrate the knowledge of bandwidth management in organizations
Indicative Content
The Emerging Technologies course will comprise of the following:
1. Emerging technologies: (8 Hours)
Introduction to DVD technology and its advantages over CD technology; Introduction to SNA Server fundamentals, SNA server network overview, Why SNA server and its connectivity with PC's;
2. Technology Management and Foresight (4 Hours)
3. Introduction to ISDN Services and alternatives to ISDN technology, Operating System software for ISDN, Connection of multiple devices to ISDN lines; Distributed computing environment (DCE), DCE services, Remote Procedure Call (RPC) & DCE security, Cell Directory Services (CDS), Global Directory Services. (8 Hours)
4. E-Business applications and the business data communications industry: Impact of e-Business Wireless technology, Groupware. Addressing the challenge of living in a connected world: (8 Hours)
5. Emerging technologies: (8 Hours)
Infra-Red; Bluetooth, 3G; Advantages/ disadvantages of living in a connected world, WiMAX, Wifi. Optical Wireless vs. RF Wireless
6. Cloud Computing, (8 Hours)
Understanding Cloud Computing, Gaining the Cloud; Advantage Four Strategies For Moving To The Cloud, Infrastructure as a Service (IaaS), Computing, Storage, Software as a Service (SaaS),
7. Web Applications, (8 Hours)
Taking Enterprise, Application Integration into the Cloud Platform as a Service (PaaS), Application Development, Security in the Cloud
8. Fiber Optics and Mobile Application Development. (8 Hours)
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Open discussion, Computer lab assignments, Individual or group presentations
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
1. Saxena P.K. & Jagdish. P, (2003). Emerging Trends in Mobile Communication, IETE Technical Review, 20, 4.
2. Linda M., G., (2000) Utilizing Internet Resources by Educational Professionals in the New Millennium, Information Technology and Libraries, 19, 3.
3. Nader F. Mir, (2007), Computer and Communications Networks, Prentice Hall Publishers.
4. Godwin-Jones, R. (2011). Emerging technologies: Mobile apps for language learning. Language Learning & Technology, 15(2), 2-11.
Haller, M. (Ed.). (2006). Emerging Technologies of Augmented Reality: Interfaces and Design: Interfaces and Design. Igi Global
- Teacher: Emmanuel Eilu
Course Description
This Course Unit is about the design and implementation of intelligent agent’s software or hardware entities that perform useful tasks with some degree of autonomy. This Course Unit provides an introduction to the basic principles and applications of Artificial Intelligence. Programming assignments are used to help clarify basic concepts. The emphasis of the Course Unit is on teaching the fundamentals, and not on providing a mastery of specific commercially available software tools or programming environments
This course enables students to carry out design and implementation of intelligent agent’s software or hardware entities that perform useful tasks with some degree of autonomy and Upon successful completion of the Course Unit, students will have an understanding of the basic areas of artificial intelligence including problem solving, knowledge representation, reasoning, decision making, planning, perception and action, and learning -- and their applications (e.g., data mining, information retrieval). It ensures the design and implementation of key components of intelligent agents of moderate complexity in Java and/or Lisp or Prolog and evaluates their performance and Graduate students will have developed familiarity with current research problems, research methods, and the research literature in AI.
Course Objectives
1. To provide students with knowledge and understanding of the basic areas of artificial intelligence including problem solving, knowledge representation, reasoning, decision making, planning, perception and action, and learning -- and their applications.
2. To explain to students the strengths and weaknesses of several methods for representing knowledge
3. To provide with students the knowledge and understanding of several AI algorithms in area such as heuristic searching, game search
4. To enable students design and implement intelligent agent’s software or hardware entities that perform useful tasks with some degree of autonomy.
5. To avail students with the knowledge and practical skills development of various key components of intelligent agents of moderate complexity in Java and/or Lisp or Prolog and evaluate their performance and Graduate students will have developed familiarity with current research problems, research methods, and the research literature in AI.
Course Learning Outcomes
By the end of this course, the student will be able to:
1. Demonstrate understanding of the basic areas of artificial intelligence including problem solving, knowledge representation, reasoning, decision making, planning, perception and action, and learning -- and their applications.
2. Assess the strength and weakness of several methods for representing knowledge
3. Assess the strength and weakness of several AI algorithms in area such as heuristic searching, game search
4. Design and implementation of intelligent agent’s software or hardware entities that perform useful tasks with some degree of autonomy.
5. Design and implement key components of intelligent agents of moderate complexity in Java and/or Lisp or Prolog and evaluate their performance and Graduate students will have developed familiarity with current research problems, research methods, and the research literature in AI.
Indicative Content
1. Introduction to Artificial Intelligence: (4 Hours)
Simulation of Intelligence behavior
2. Computational models of intelligent behaviour, (8 Hours)
i) problem solving,
ii) knowledge representation,
iii) reasoning, planning, decision making, learning, perception, action, communication and interaction.
3. Problem solving: (8 Hours)
i) games, natural language question answering,
ii) visual perception, learning;
iii) Aim-oriented algorithms versus solution-guaranteed algorithms.
4. Understanding Natural Languages: (8 Hours)
i) Parsing techniques,
ii) context-free and transformational grammars,
iii) transition nets, augmented transition nets,
iv) grammar-free analyzers,
v) sentence generation.
5. Knowledge Representation: (8 Hours)
i) First-order predicate calculus;
ii) PROLOG and LISP languages;
iii) Semantic nets; partitioned nets;
iv) Production rules;
v) knowledge base,
vi) the inference system,
vii) forward and backward deduction.
6. Expert System: (8 Hours)
i) Existing systems,
ii) Domain exploration;
iii) Meta-knowledge, expertise transfer, self-explaining systems.
7. Pattern Recognition Structured Descriptions: (8 Hours)
i) Symbolic description,
ii) machine perception,
iii) line finding, interpretation, semantics and models, object identification and speech recognition.
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Tutorials, Lectures, Seminars.
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
1. Stuart Russell and Peter Norvig, (2009). Artificial Intelligence: A modern approach 3rd Edition
2. Yuan Wang and David J. DeWitt. Computing Page Rank in a Distributed Internet Search Engine System. In Proceedings of the 13th International Conference on Very Large Data Bases, 2004.( Presentation)
- Middleton, S. E., Shad bolt, N. R. and De RoureUser Profiling in Recommender Systems ACM Transactions on Information Systems (TOIS) 22(1) pp. 54-88.,2004.( Presentation)
- Sieg A., MobasherB., Burke R.,Prabu G., Lytinen S. Representing User Information Context with Ontologies In proceedings of HCI international conference 2005.

- Teacher: Emmanuel Eilu
Course Description
This course is designed to equip students with knowledge of how Telecommunication Networks can be harnessed to support enterprise business processes. It specifically looks at the regulatory framework, management architectures, network documentation and relevant standards applicable to the Telecommunication Networks.
Course Objectives
1. To introduce to students the concept and principle of network management, monitoring and troubleshooting network management protocols that are practical for corporate network, use of packet sniffer to troubleshoot network problems, use of telecommunications business organizations, discuss the issues created by new innovative technologies
2. To enable students develop necessary documentation to support organizational requirements for telecommunications network
3. To inform students of the current status and future directions of telecommunications regulatory environment;
4. To provide knowledge and understanding of the strategic management issues and the options created by emerging technologies;
Course Learning Outcomes
By the end of this course, the student will be able to:
1. Identify and understand the concept and principle of network management, monitoring and troubleshooting network management protocols that are practical for corporate network, use of packet sniffer to troubleshoot network problems, use of telecommunications business organizations, discuss the issues created by new innovative technologies
2. Develop necessary documentation to support organizational requirements for telecommunications network
3. Follow the current status and future directions of telecommunications regulatory environment;
4. Discuss the strategic management issues and the options created by emerging technologies;
Indicative Content
1. Documenting the Network: (20 Hours)
i) requirements capture and specification,
ii) functional specification,
iii) design specification,
iv) documenting the network configuration.
2. Managing the Network: (20 Hours)
i) influences on the network,
ii) management architectures and standards,
iii) performance management,
iv) spectrum management,
v) fault management,
vi) disaster management,
vii) managing changes in a network,
viii) cost minimization management
3. Corporate and Regulatory Requirements: (20 Hours)
i) management teams,
ii) operations and support,
iii) standards and protocols;
iv) implications of broadband networks for traffic integration.
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures and Lab sessions
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
- Suzan Snedaker The Best Damn IT Security Management Book Period
- Robert C Newman Computer Security: Protecting digital resources :

- Teacher: Emmanuel Eilu
Course Description
This course program shows the analysis and transformation of how to represent and analyse programs, also how to transform programs and what transformations to apply. It also helps to study imperative, functional, and object-oriented languages. The Program representation and analysis is widely useful in software engineering tools, DB query optimizers, Programmable graphics renderers and safety checking of code, e.g. in programmable/extensible systems, networks, databases. This course introduces some of the compiler-related topics in formal languages and gain preparation for graduate studies/ research in both complier construction and formal languages.
Course Objectives
- To introduce to students the organization of a compiler and several sets of grammar production rules.
- To explain to students both recursive descent and non-recursive methods of parsing
- To provide knowledge and practical skills in designing and implementing a simple compiler for a higher-level language including the lexical analyzer, parser, symbol tables and code generation.
- To provide knowledge and understanding of how the programming language compilers such as C++ and Java generate syntax errors.
Course Learning Outcomes
By the end of this course unit, the student will be able to:
1. Gain full understanding of organization of a compiler and several sets of grammar production rules.
2. Learn both recursive descent and non-recursive methods of parsing
3. Design and implement a simple compiler for a higher-level language including the lexical analyzer, parser, symbol tables and code generation.
4. Fully understand how the programming language compilers such as C++ and Java generate syntax errors.
Indicative Content
1. Compiler structure: (8 Hours)
i) analysis-synthesis model of complication,
ii) various phases of a compiler,
iii) tool based approach to compiler construction.
2. Scanning: (8 Hours)
i) The Scanning Process,
ii) Regular Expressions,
iii) Finite Automata,
iv) From Regular Expressions to DFAs,
v) Implementation if a TINY Scanner,
vi) Use of Lex to Generate a Scanner Automatically
3. Lexical analysis: (8 Hours)
i) interface with input,
ii) parser and symbol table,
iii) token, lexeme and patterns.
iv) Difficulties in lexical analysis.
v) Error reporting. I
vi) mplementation.
vii) Regular definition,
viii) Transition diagram, LEX
4. Syntax analysis: (8 Hours)
i) CFGs, ambiguity, associativity, precedence,
ii) top down parsing, recursive descent parsing,
iii) transformation on the grammars,
iv) predictive parsing, bottom up parsing,
v) operator precedence grammars,
vi) LR parsers (SLR,LALR,LR) YACC.,
vii) syntax directed definition:
viii) inherited and synthesized attributes dependency graph,
ix) evaluation order, bottom up and to down evaluation of attributes,
x) L-and S attributed definitions.
5. Semantic Analysis: (8 Hours)
i) Attributes and Attribute Grammars,
ii) Algorithms for Attribute Computation,
iii) The Symbol Table,
iv) Data Types and Type Checking,
v) A Semantic Analyzer for the TINY Language
6. Type checking: (8 Hours)
i) type system,
ii) type expression,
iii) structural and name equivalence of types,
iv) type conversion,
v) overloaded functions and operators,
vi) polymorphic functions.
7. Run time system: (4 Hours)
i) storage organization,
ii) activation tree,
iii) activation record,
iv) parameter passing,
v) symbol table,
vi) dynamic storage allocation.
8. Code Generation: (8 Hours)
i) Intermediate Code and Data Structures for Code Generation,
ii) Basic Code Generation Techniques,
iii) Code Generation of Data Structure References,
iv) Code Generation of Control Statements and Logical Expressions,
v) Code Generation of Procedure and Function Calls,
vi) Code Generation in Commercial Compilers,
vii) A Survey of Code Optimization Techniques,
viii) Simple Optimizations for the TINY Code Generator
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Lab sessions, Practical demonstration
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
1. Kenneth C. L., (1997). Compiler Construction: Principles and Practice, PWS Publishing Company, ISBN 0-534-93972-4.
2. C.N Fisher and R.J LeBlanc ‘Crafting a compiler with C’. Benjamin/Cummings
- Alfred V. Aho, Ravi Seth, Jeffrey D. Ullman, Compilers, Principles, Techniques, and Tools

- Teacher: Emmanuel Eilu
