Course Description
The course is designed to equip students with knowledge of managing various concepts related to enterprise computing systems and their relationship with today’s business operations. The course covers a variety of Enterprise systems including Enterprise Resource Planning (ERP) systems, Supply Chain Management (SCM) systems, Supplier Relationship (SRM) systems, Customer Relationship Management (CRM) systems. This course is therefore viewed as a combination of business management practice and technology.
Course Objectives
1. Enterprise-wide computing and its support for organizational business activities.
- To explain the factors leading to the development of ERP systems.
- To provide knowledge and understanding on the advantages and disadvantages of implementing an ERP system in a business environment.
- To provide knowledge and understanding on how an integrated information system can support t business processes that can enhance efficiency.
- To provide knowledge and understanding on the process improvement and ERP implementation
Course Learning Outcomes
At the conclusion of this course students will be able to:
1. To describe enterprise-wide computing and its support for organizational business activities.
- Identify the factors leading to the development of ERP systems.
- Appreciate the advantages and disadvantages of implementing an ERP system in a business environment.
- Discuss how an integrated information system can support t business processes that can enhance efficiency.
- Create process models to assist the process improvement and ERP implementation
Indicative Content
1. The enterprise and related concepts; (8 Hours)
i) strategies of meeting enterprise goals,
ii) challenges facing enterprises,
2. Enterprise Computing Environment, (8 Hours)
i) enterprise computing types,
ii) client-server model of computing for enterprise wide computing environment,
iii) characteristics of enterprise-level computing,
3. Enterprise Developers and Roles, (8 Hours)
key enterprise development roles,
4. Enterprise application and qualities. (4 Hours)
5. Enterprise information systems, (8 Hours)
i) Supply Chain Management,
ii) Customer Relationship Management,
iii) benefits and challenges of enterprise systems,
6. The internet and OSI model. (8 Hours)
7. Network Protocols, (8 Hours)
topologies and access methods,
8. Enterprise Network Security, (8 Hours)
i) Issues,
ii) Concepts and Techniques.
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Tutorials, Lectures, Seminars.
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Recommended Books
1. Jana P, Robert Mark B, and Anton (2005) Polgar.Building and Managing Enterprise-Wide Portals. Book Publisher: Hershey, PA: Idea Group Publishing.
2. Thomas W. Madron.Enterprise-Wide Computing: How to implement to Implement and Manage LANs Wiley professional computing. Publisher Wiley, 1991.ISBN0471532975, 9780471532972.
3. Effective management of local area networks by Kornel Terplan,McGeaw Hill,1992
4. Network re-engineering: Foundations of enterprise computing by Alan Simon. Copy right 1994

- Teacher: Emmanuel Eilu
Course Description
Basically this course unit is meant to introduce students with fields of cryptology in general.
The course examines the theory and methods for coding information aimed to transmit over a noisy channel and be accurately decoded by the receiver. The concepts of cryptology and coding theory are discussed in detail.
Course Objectives:
The objectives of this course unit are to equip students with:
1. Knowledge and understanding of the classical cryptosystems and the techniques used to break them;
2. Knowledge and understanding of the ideas of public key cryptosystems and digital signature schemes, and be able to use the algorithms for RSA and ElGamal;
3. Skills for analysing the efficiency and security of cryptosystems in a rigorous mathematical setting
4. Knowledge and understanding of the ideas involved in error correcting codes; understand linear codes, syndrome decoding and perfect codes.
5. Basic properties of cyclic codes, including the decoding algorithm.
Course Learning Outcomes:
This course aims to give students an introduction to the two areas of cryptology and coding theory. At the end of this course students should be able:
1. To describe classical cryptosystems and the techniques used to break them;
2. Demonstrate understanding of the ideas of public key cryptosystems and digital signature schemes, and be able to use the algorithms for RSA and ElGamal;
3. To analyse the efficiency and security of cryptosystems in a rigorous mathematical setting
4. Demonstrate understanding of the ideas involved in error correcting codes; understand linear codes, syndrome decoding and perfect codes.
5. To explain the basic properties of cyclic codes, including the decoding algorithm.
Indicative Content
1. Classical and modern symmetric cryptosystems; (12 Hours)
i) Caesar, substitution, affine, and Vigenere ciphers,
ii) Vernam one-time-pad, DES, AES and Rijndael.
2. Asymmetric "public key" cryptosystems; (12 Hours)
i) RSA, Rabin, Diffie-Hellman key exchange,
ii) Elgamal,
iii) Hash Functions and Digital Signatures.
3. Factoring integers and generating large prime numbers. (12 Hours)
4. Computer security (Kerberos, PGP, IP secure) (12 Hours)
5. Coding Theory; (12 Hours)
i) binary codes,
ii) Linear Codes,
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lecture method, Tutorials, Demonstrations, Student discussions, Student research assignments
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
1. W. Trappe & Lawrence Washington, Introduction to Cryptography with Coding Theory, 2nd edition, Prentice Hall, 2005.
2. D. R. Hankerson, D. G. Hoffman, D. A. Leonard, C. C. Lindner, K. T. Phelps, C. A. Rodger, J. R. Wall, Coding theory and cryptography: The essentials, 2nd edition, revised and expanded. New York: Marcel Dekker, 1991. ISBN: 0824704657
3. Stallings William. Cryptography and network Security: Principle and Practice. Prentice-Hall, NJ,1999
4. J. Buchmann, Introduction to Cryptography (Springer)

- Teacher: Emmanuel Eilu
Course Description
This course unit covers the concepts necessary to understand for successful management of information systems projects. Major topics include: Planning for systems development and estimations, Scheduling and implementation issues control and project closure. This course will prepare students as future IT good project managers who can play leading roles in the application and management of e-business system development. It will enable students to understand issues related to the development and management of information systems. The course will educate students on how to prepare IT project supporting documents
Course Objectives
The objectives of the course include:
1. To explain the knowledge areas related to IT Project planning and Management
2. To provide knowledge on the roles of project managers and participants.
3. To provide knowledge and understanding on the sequence of activities in a typical IT project and the nature of the deliverables that are common in a typical IT project
4. To provide knowledge and understanding of the stages of the project management life-cycle and relate this to the roles, activities, and outcomes of the project
5. To provide practical skills on project management using a case study.
Course Learning Outcomes
Upon completion of this course unit students will be able to:
1. Describe the knowledge areas related to IT Project planning and Management
2. Describe the roles of project managers and participants.
3. Understand the sequence of activities in a typical IT project and the nature of the deliverables that are common in a typical IT project
4. Describe stages in the project management life-cycle and relate the project management life-cycle stages to the roles, activities, and outcomes of the project
5. Apply the concepts of project management to real life IT projects.
Indicative Content
This course unit will explore the following topics:
1. Concept of Project, Project Management, (4 Hours)
2. Process Management, (4 Hours)
3. Project Management challenges, (4 Hours)
i) competencies, and functions,
ii) Tools (PERT and Gantt chart).
4. The project management lifecycle; (4 Hours)
i) initial scope,
ii) identifying task durations,
5. Methodologies for developing software, (4 Hours)
i) specifying task,
ii) Software project management,
6. Project Cost Management, (4 Hours)
7. Project Quality Management, (4 Hours)
8. Project Time Management, (4 Hours)
9. Project risk management (4 Hours)
10. Project scope Management, (4 Hours)
11. Dependencies, assigning resources, directing team efforts, (4 Hours)
12. monitoring and control, (4 Hours)
i) completed project experiences
ii) evaluation.
13. Preparing a Project Proposal, (4 Hours)
14. Post Project Appraisal, (4 Hours)
15. Project leadership skills. (4 Hours)
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Tutorials
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Textbooks:
1. Schwalbe, Kathy, (2010); Information Technology Project Management (Sixth Edition); CENGAGE. ISBN-10: 0324786921 | ISBN-13: 9780324786927
2. Project Management Institute, (2013). Guide to the Project Management Body of Knowledge (PMBOK Guide) Fifth Edition.
3. Harold R. K, (2013). Project Management: A Systems Approach to Planning, Scheduling, and Controlling.
4. Terry, S (2009). Strategic Project Management Made Simple: Practical Tools for Leaders and Teams

- Teacher: Emmanuel Eilu
Course Description
This Course Unit is designed for analysts, statisticians, marketers, and programmers who are tasked with developing predictive models for marketing, risk, retention, and lifetime value. It is also for vice-presidents, directors, and managers who want a ‘hands-on’ introduction to what is involved in developing predictive models
Course Objectives
1. To introduce students to data warehousing and data mining concepts
2. To explain to students the importance of making meaningful use of large volumes of data for decision making.
3. To provide students with the knowledge and understanding of the methods and technologies for successful development of data warehouses
4. To provide students with knowledge and understanding of the leading data mining methods and their application to real-world problems.
Course Learning Outcomes
By the end of the course, the student will be able to:
1. Describe data warehousing and data mining concepts
2. Understand the methods and technologies for successful development of data warehouses
3. Demonstsate the knowledge of leading data mining methods and their application to real-world problems
Indicative Content
1. Introduction to data warehousing concepts (8 Hours)
2. Data warehousing Architecture; (8 Hours)
i) General Principles/Concepts, On-Line Analytical Processing, Data warehouse architecture, Enterprise architecture, Data mart, Virtual data warehouse, Meta data
3. Modeling: (8 Hours)
ii) Multi-dimensional modeling of data, Dimensional modeling and hierarchy
iii) Warehouse schema
iv) Normalization, Star schema, snowflake schema
4. OLAP operations (8 Hours)
i) Slicing and dicing, Drill up and drill down, Drill within and drill across
5. OLAP engine: (8 Hours)
i) Specialized SQL server, ROLAP, MOLAP, HOLAP
6. Data transformation services (8 Hours)
7. Data warehouse implementation (8 Hours)
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Readings of articles and chapters in textbooks, Guided project.
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List
1. Jiawei Han and MichelineKamber, Data Mining: Concepts and Techniques, Morgan Kaufmann, 1998.
2. U.M. Fayyad, G. Piatetsky-Shapiro, P. Smyth and R. Uthurusamy (Eds.), Advances in Knowledge Discovery and Data Mining, AAAI/MIT Press, 1996.
3. Paulraj, P, (2001). Data Warehouse Fundamentals: A Comprehensive Guide for IT Professionals, ISDN 0-471-22162-7.
Turban, A, & Liang (2007). Decision Support Systems and Intelligent Systems, 7th Edition, Prentice Hall
- Teacher: Emmanuel Eilu
Course Description
Mobile computing is the use of portable computer systems anywhere, anytime while connected to a wireless network infrastructure, such as the Internet to support global connectivity and remote computing. It allows transmission of data via a computer system without being connected to physical links. To explore many different aspects of mobile computing through using mobile phones connected to a network for computing purposes no matter the geographical location.
Course Objectives
- To introduce to students the various concepts of delivery channels, hardware devices and mobile data devices.
- To equip students with the knowledge and understanding of using mobile phones to carry out online business without travelling long distances.
- To enable students identify the best IT gadgets used to transmit bulky data on the network connected.
- To provide students with the knowledge and understanding of the threats that arise out of mobile computing and the possible measures taken to overcome them.
Course Learning Outcomes:
By the end of this course, the student will be able to:
1. Understand various concepts; Delivery channels such as Analogue, Digital, Universal mobile telephone services standard based on CDMA, Hardware devices: mobile data devices to outnumber personal computers, mobile phones, Personal Digital Assistant, Unusual and futurities devices, Software standards: SMS, WAP, Bluetooth, windows, mobile explorers, Cellular network architecture such as GSM,GPRS,CDMA, Internet.
2. Use mobile phones to carry out online business without travelling long distances
3. Identify the best IT gadgets used to transmit bulky data on the network connected,
4. Understand the threats that arise out of mobile computing and the possible measures taken to overcome them before danger occurs and Identify Protection techniques on the network from the unauthorized people.
Indicative Content
Preview and introduction to the course
1. Introduction to wireless communication, (8 Hours)
i) Advances in wireless technology,
ii) Limitation,
iii) political and technical difficulties,
iv) Device limitations (browsers, screen size),
v) Data Communications,
vi) TCP/IP,
vii) Open System Interconnection (OSI),
viii) Overview of TCP/IP
2. Basic overview of transmission: (8 Hours)
3. Channel capacity, (4 Hours)
i) Transmission media,
ii) Multiplexing
4. Basic communication network technologies: (4 Hours)
5. Packet switching, (4 Hours)
i) Frame relay,
ii) ATM
6. Communication Technology: (4 Hours)
7. Underlying technology of wireless communication, (4 Hours)
i) Encoding of analog and digital data for wireless transmission
8. Propagation (4 Hours)
9. Antenna performance, (4 Hours)
i) Wireless transmission modes- Analog and digital data and signals.
10. Spread spectrum (4 Hours)
11. Frequency hopping, (4 Hours)
i) Direct sequence spread spectrum,
ii) Code division multiple access (CDMA)
iii) Wireless Access Protocol
12. Bluetooth, (4 Hours)
i) Personal computers,
ii) Mobile phones,
iii) Other wireless devices
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lecturer, Tutorial, Lab sessions, Case studies
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List:
1. Mobile computing application and service creation, McGraw-Hill)
2. Schiller, (2002) “mobile communications” Addison Wesley
3. Mehrotra “GSM system Engineering”, Ertech House, 1997
- M.V.D. Heijden, M Taylor (2000). “Understanding WAP” Artech House,

- Teacher: Emmanuel Eilu
Course Description
This course provides in-depth understanding of developing and analyzing distributed systems. The focus is on developing distributed systems on desktop and perhaps mobile environments and analyzing their performance, reliability, scalability, consistency and security. Students will develop distributed applications using sockets / datagrams / multicast sockets, processes/threads/pipes/FIFOs, COM/DCOM, HTTP and Forms using database environment for the server side as well as web based applications for the client side
Course Objectives
1. To provide students with an understanding of the key components of distributed systems and the challenges they face by future distributed systems.
2. To provide students with knowledge required to design, implement and manage distributed systems.
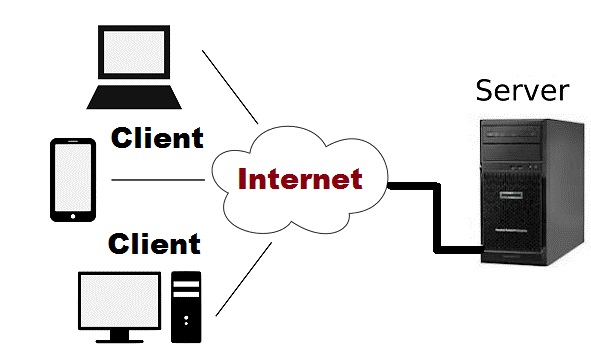
- To provide knowledge to students about the characteristics and issues associated with client-server computing and explain the best approaches for implementing client-server computations using the TCP/IP suite.
- To provide knowledge and understanding of the concepts of client/server and distributed computing, and the various models which can be used to implement these computing paradigms.
- To provide students with knowledge required on the development methodology and the software, hardware and training requirements of the clients/Server Systems.
- To provide students with knowledge and skills for the various phases for migrating to Client/Server computing in a distributed environment.
Course Learning Outcomes
By the end of this curse, the student will be able to:
1. Understand of the key components of distributed systems and the challenges they face by future distributed systems.
2. Design, implement and manage distributed systems.
- Explain the characteristics and issues associated with client-server computing and explain the best approaches for implementing client-server computations using the TCP/IP suite.
- Understand the concepts of client/server and distributed computing, and the various models which can be used to implement these computing paradigms.
- Demonstrate an understanding of the development methodology and the software, hardware and training requirements of the clients/Server Systems.
- Demonstrate an understanding of the various phases for migrating to Client/Server computing in a distributed environment.
Indicative Content
Unit 1: Introduction Client/Server Computing (8 Hours)
· Introduction of DS, Identify the reasons for Client/Server computing being preferred to mainframe computing, Identify why client/Server Computing preferred in On-line Transaction Processing, Identify the role of client/Server computing in Decision Support Systems, Identify the features of data transparency in Client/Server computing, Identify how resources sharing is implemented in Client/Server computing, Identity frameworks and their features for interchange ability and interoperability of data in Client/Server computing, Identify how various applications can be integrated under the Client/Server environment.
Unit 2: Basics of Clients/Server Computing (8 Hours)
· Identify the functions and benefits of a client & server in the Client/Server computing model, Sequence the steps involved in the processing of an application based on a Client/Server computing model, Match the different network interconnection devices with their features, Identify the different data transmission methods used in a network.
Unit 3: Client Server Environment (8 Hours)
· Identify the server Client Environments available, Identify the correct location of the presentation function in the different style of cooperative processing, Identify the correct location of data management functions in the distributed data management style of cooperative processing, Identify the services provided by interposes communications, Identify the different layers of the OSI and TCP/IP Model with their functions
UNIT 4: Application Development in Client Server Environment (8 Hours)
· Identify the activities in the Systems Integration Life Cycle Project Management, Match the given components of a Systems Development Environment with their corresponding activities, Match the following data storage devices with their features, Match the problems faced by System Administration in a Client Server environment with the related areas in which they should be trained.
Unit 5: Migrating to a Client/Server Environment (8 Hours)
· Identify types of applications suitable for Client Server systems, factors resulting in productivity gain for the end-users, Recognize the organizational and end-user priorities of an organization with regard to systems, Match the maintenance issues in a Client/Server environment with the procedures to resolve them.
Unit 6: Naming and Fault Tolerance (8 Hours)
Unit 7: Distributed Systems Security (8 Hours)
Unit 8: Distributed File Systems (4 Hours)
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Tutorials, Lab sessions, Case analysis
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List
1. Coulouris et al, Distributed Systems: Concepts and Design, 4~5th edition, Addison-Wesley 2005-2012
2. Tanenbaum, A. S., & Van Steen, M. (2007). Distributed systems. Prentice-Hall.Maarten van Steen,
3. Distributed Systems: Principles and Paradigms, Vrije Universiteit Amsterdam, Faculty of Science - Dept. Mathematics and Computer Science
- Teacher: Emmanuel Eilu
Course Description
C is the object oriented superset of ANSI C. This course provides students with a comprehensive study of the C Programming Language. The main concepts to cover include the algorithm development, program structure and creation, data structures, syntactical and semantic correctness, planning and segmentation in programming as well as working with files, structures and program development.
Course Objectives
1. To provide hands-on training to students to design and write programs in the C language. Basic concepts of program structure, programming, data structures, algorithms, algorithms development using the top-down design approach.
2. To provide the general concepts related to programming, using the C procedural programming language and ends with an introduction to the Standard Template Library (STL). It includes all the types of Data Structures used in organizing Data.
3. To give students practical training that enables them to write robust computer software using C programming language
Course Learning Outcomes
By the end of this course, the student will be able to:
1. Demonstrate understanding and practical skills to design and write programs in the C language. Basic concepts of program structure, programming, data structures, algorithms, algorithms development using the top-down design approach.
2. Demonstrate understanding of the general concepts related to programming, using the C procedural programming language and ends with an introduction to the Standard Template Library (STL). It includes all the types of Data Structures used in organizing Data
3. To write robust computer software using C programming language
Indicative Content
1. Overview of the C programming Language: (8 Hours)
i) Functions,
ii) Arrays,
iii) Structures
iv) Pointers plus strings
2. Strings: (8 Hours)
i) Representation of Strings in contiguous storage,
ii) string,
iii) conversions,
iv) representations of variable-length strings,
v) examples of operating in strings.
3. Overview of Data Structures: (8 Hours)
i) Definition,
ii) Types and Examples of DS,
iii) Applications
4. Operation of Stacks and Queues: (8 Hours)
i) Push and Pop operations,
ii) Display/view,
iii) Polish Notations,
iv) Types of Queues, and Applications of both Queues and Stacks.
5. Linked Lists: (4 Hours)
Types and Applications of Linked Lists
6. Trees and their Applications: (8 Hours)
i) Terminologies,
ii) Binary Trees,
iii) AVL Trees and Applications
7. Graphs and their Applications: (8 Hours)
i) Terminologies,
ii) Representations,
iii) Graph Traversals,
iv) Spanning Trees
8. Searching and Sorting: (8 Hours)
i) basic searching techniques,
ii) Linear and Binary search,
iii) Internal and External Sorting
9. Storage Management (4 Hours)
Study Materials
Relevant text books, power point slides, a projector, lap top and teaching aids necessary.
Mode of Delivery
Lectures, Tutorials, Lab sessions
Mode of Assessment:
Test 15%
Assignment 15%
End of semester examination 70%
Total 100%
Reading List
- Prof V. B. Nanda, (2009). C Programming and Data Structures, Sikkim Manipal University, Spring
- Gross J. L. & Yellen J., (2005). Graph Theory and Its Applications.
3. Forouzan, B.A. & Gilberg, R.F. (2007). Computer science, A structured programming approach using C, Third edition, Thomson.
4. Tanenbaum, A.S., Langsam, Y. & Augenstein, M.J., (2009) Data Structures Using C -, PHI/Pearson Education.
Kalicharan, N. (2008). Data Structures in “C”. Noel Kalicharan
- Teacher: Emmanuel Eilu
